Leave Threats Nowhere to Hide
Did you know that the average time to detect a security breach is 212 days? Did you know that it takes 75 days on average to contain the incident once detected? The longer the threat lifecycle is, the bigger the cost of the incident. This teaches us that proactively hunting for threats is essential in any robust cybersecurity program.
A Top Security Initiative ― Many Barriers
Establishing a threat hunting program in-house comes with many challenges.

Proactive Threat Hunting Operations
Analytics-Driven Approach
It uses statistical methods to detect something that hasn’t been seen before or irregularities in baseline data in the environment.

Hypothesis-Based Approach
It’s performed by hunters thinking like the adversary. It involves developing and testing theories about where and how a determined attacker might attempt to operate unseen.

Intelligence-Based Approach
It leverages up-to-the-minute threat intelligence to search historical data for signals of intrusion. Indicators of compromise (IoCs) are a good starting point, although it should not be limited to them but extended to behaviors associated with a specific threat or group of threats.
Proactive threat hunting boosts the overall security posture by:
- Reducing the probability of being compromised
- Uncovering ongoing threats swiftly
- Accelerating the response
- Reducing the incident and recovery cost
- Identifying security gaps and misconfigurations
- Creating recommendations for attack-surface reduction plans
Read this eBook to deep dive into the threat hunting process, better understand the pros and cons of hunting and learn alternative ways to do it.
87%
of organizations agree that threat hunting should be a top security initiative
Businesses of all sizes agree that they should hunt for active or dormant threats in their environments that have bypassed security controls
53%
of organizations plan to adopt threat hunting in the next 12 months
By proactively hunting for threats, they will be able to reduce the time to detect threats, accelerate the response and minimize the incident costs
65%
of the organizations indicated that limitations of their tools or technology are barriers
Threat hunting comes with many challenges that could frustrate the initiative: limitations of existing tools or technology, lack of expertise, too much data to process
51%
of the organizations face or have faced barriers due to a lack of security skills
For this reason, most companies and partners delegate, at least partially, the threat hunting service to their managed security provider
4 Threat Hunting Paths You Should Appraise
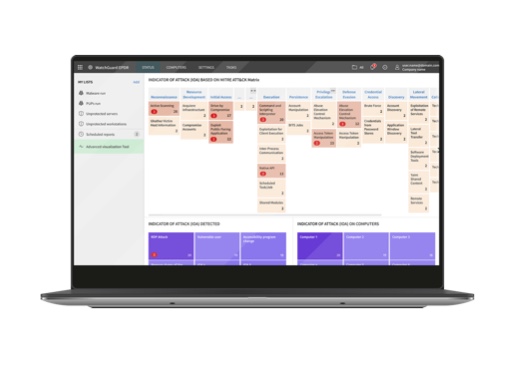
Threat Hunting as a Service
The Threat Hunting Service in WatchGuard EDR and WatchGuard EPDR uncovers threats lurking in endpoints by spotting a set of deterministic indicators of attack (IoAs). Actionable guidelines, provided in those products, enable you to quickly respond to threats with confidence.
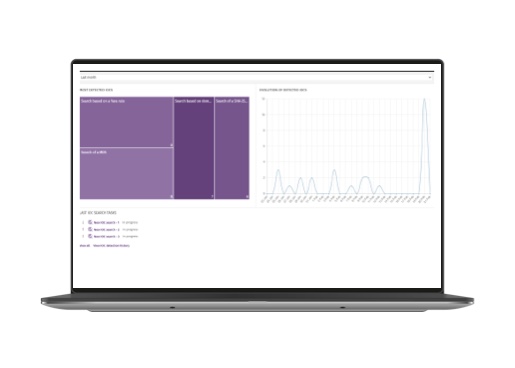
Search for Undetected Threats
Additionally, WatchGuard Advanced EDR and EPDR enable security teams to assess their environments for emerging threats by searching for OSINT (Open-Source INTelligence) or privately sourced IoCs – hashes, filename, path, domain, IP, and Yara rules. Analysts can contain the spread of risk if a compromise is detected by isolating affected endpoints from the network while eradicating and recovering from the incident.
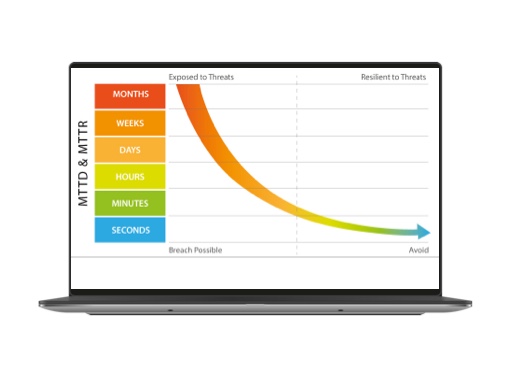
Delegate to a Team of Cybersecurity Experts
WatchGuard MDR constantly monitors endpoint activity, investigating every weak signal of abnormal behavior and uncovering more threats when they show suspicious activity. You are backed by our expert threat analysts, who immediately provide you with detailed, actionable reports to respond to. Weekly and Monthly reports are shareable proof of diligence in protecting, detecting, and hunting threats.
Elevate Your Threat Hunting with Automation
WatchGuard Orion is a Cloud-based multi-tenant threat hunting and incident management platform that uses machine learning to empower security analysts to uncover unknown threats, investigate suspicious activity, and respond quickly to incidents. Its built-in queries and threat hunting rules help SOCs ask the right questions to find issues in the enriched 365-day telemetry, create hypotheses, and run detailed investigations.