Identity Security Begins with MFA
In today’s security landscape, stolen credentials are hackers' primary tactic to break in. Implementing multi-factor authentication (MFA) is an essential security measure to protect your business. AuthPoint MFA offers easy-to-deploy security and reliable user verification methods that adapt to any workforce. Additionally, its extensive integration ecosystem and single sign-on (SSO) capabilities provide comprehensive access control, enabling organizations to manage user access privileges quickly and efficiently.
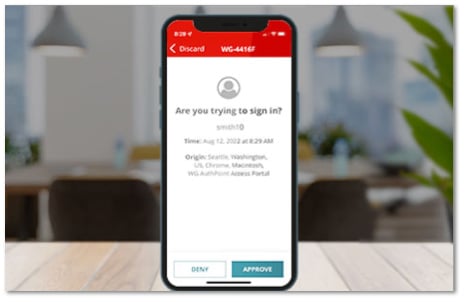
Mobile Authenticator App
The app is conveniently designed for Android and iOS and features multiple tokens and authentication methods. It verifies user identities using push-based notifications for one-touch approval/denial of access requests. Time-based one-time passcodes (TOTP) retrieve dynamic, time-based, one-time passcodes, and QR codes generate unique and encrypted codes that serve as a verification factor.

Windows and macOS Login
Windows and macOS machines usually require login with a simple username and password, which risks exposing critical information if credentials are compromised. AuthPoint provides additional protection for Windows and Mac users with online and offline verification methods through the mobile app.

Web Single Sign-On (SSO) Application Portal
SSO authentication allows companies to manage web access by enabling workforce users to sign in to multiple independent applications using one set of credentials. SSO reduces the risk of password-driven vulnerabilities with MFA-protected access to corporate applications.

WatchGuard Cloud Management
Managing AuthPoint is simple and intuitive in WatchGuard Cloud’s centralized environment. Configure zero trust risk-based policies to assess and enforce user access controls. Rank the resources you want to protect and restrict access based on users, groups, and control attributes like day, time, location, and more.

Unique Mobile Device DNA
AuthPoint offers a unique approach to secure migration. The mobile device DNA provides an additional identifying factor to ensure only authorized users can log in to systems and applications. Any attacker attempting to gain access using a cloned phone or app would be issued a non-functional one-time password and not allowed to continue.

Robust Integrations and Ecosystem
WatchGuard’s ecosystem includes over one hundred third-party integrations with AuthPoint. It supports deployment with any business so users can verify their identity before accessing sensitive Cloud applications, VPNs, and networks.

Go Beyond MFA with Total Identity Security
AuthPoint Total Identity Security enhances user-centric capabilities by providing extensive credentials management. This solution includes a corporate password manager and dark web monitoring services, which allow you to confidently protect workforce identities and authorize verified user access to your systems and networks.




4422.jpg?itok=ziqrvO2s)

